Securing your ASUS router with SSH keys stored on a Yubikey
Overview
This will explain how to setup your ASUS router’s SSH access through the most secure solution currently available: using SSH keys stored on hardware keys. For this I am using the Yubikey 5 NFC family of keys - I have 2 USB-A and 1 USB-C.
The code snippets are from a generic macOS terminal screen.
My work environment
Router used - ASUS RT-AX86U
Router firmware - Asuswrt-Merlin 386.7_2
Installed software (not needed for this) - Entware, Debian. AMTM v3.3
Dropbear v2022.82
Yubikey 5 NFC, Firmware 5.4.3
My workstation - Apple M1 Pro, macOS 12.6.
Brew info:
==> **openssh**: stable 9.0p1 (bottled)
==> **bash**: stable 5.1.16 (bottled), HEADGenerating the SSH keys
We are going to generate a ed25519-sk key pair. The system automatically splits the private key and keeps one half locally (~/.ssh/ed25519_sk) and the other half on the hardware key.
> ssh-keygen -o -a 256 -t ed25519-sk
Generating public/private ed25519-sk key pair.
You may need to touch your authenticator to authorize key generation.
Enter PIN for authenticator:
You may need to touch your authenticator (again) to authorize key generation.
Enter file in which to save the key (/Users/cristian/.ssh/id_ed25519_sk):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /Users/cristian/.ssh/id_ed25519_sk
Your public key has been saved in /Users/cristian/.ssh/id_ed25519_sk.pub
The key fingerprint is:
SHA256:8iyT8nCbeCR0uxsoWAQ9B21n6iiNK1IUso8JORFXtEQ cristian@macbook
The key's randomart image is:
+[ED25519-SK 256]-+
|ooo*E |
|oo+.+.o |
| =.=.+ |
|=.. o . |
|.O.+ ...S |
|=o= o.o= |
|.+. +o*.o |
|+ . *o* |
|o ..=. |
+----[SHA256]-----+
>Remember to chmod 400 the keys in your ~/.ssh folder.
>chmod 400 ~/.ssh/id_ed25519_sk*Uploading the public key to the router
We are going to upload the public key to the router now.
- Copy your public key
>cat ~/.ssh/id_ed25519_sk.pub
sk-ssh-ed25519@openssh.com AAAAGnNrLXNzaC1lZDI1NTE5QG9wZW5zc2—---------------------------------------------------------------------------------------BHNzaDo= cristian@macbook- Open your router admin page and go to Administration → System → Service.Ensure the router is properly configured for SSH access and simply paste your key in. Please note you can have multiple keys, each one on a separate line.
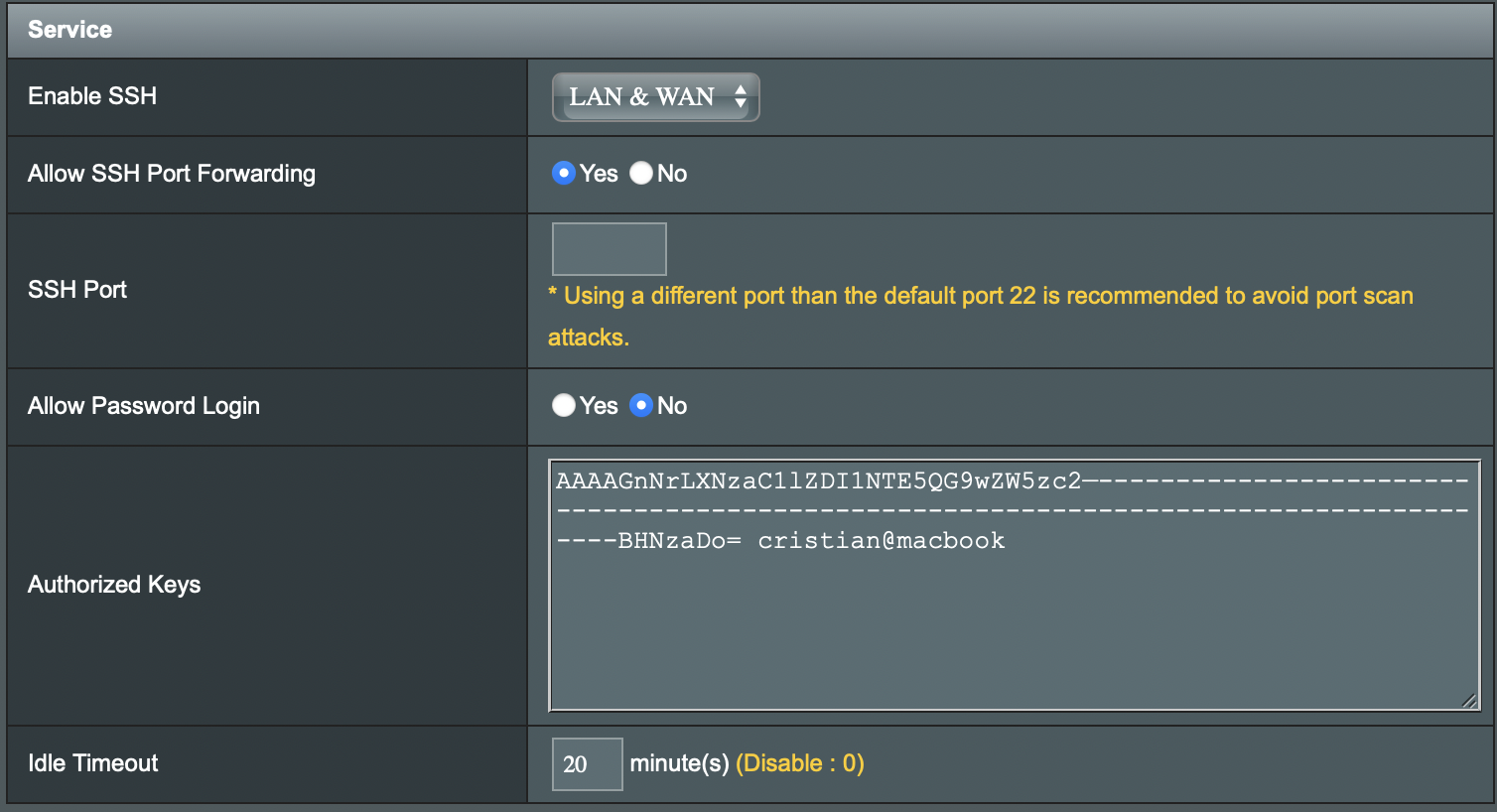
- Apply
Connecting to the router
To connect, simply use the command below. Touch the key when requested.
>ssh cristian@----------.com -o AddKeysToAgent=no -i ~/.ssh/id_ed25519_sk
Enter passphrase for key '/Users/cristian/.ssh/id_ed25519_sk':
Confirm user presence for key ED25519-SK SHA256:8iyT8nC----------------------------8JORFXtEQ
User presence confirmed
ASUSWRT-Merlin RT-AX86U 386.7_2 Sun Jul 24 21:37:08 UTC 2022
cristian@router:/tmp/home/root#WARNING - macOS by default has a ssh-agent which automatically adds authenticated keys into its volatile cache. At the time of writing this, the ssh-agent is not able to use the ed25519-sk key saved in its cache on a second authentication attempt, hence
the
-o AddKeysToAgent=nooption.
Still to do …
- Test the connectivity on Linux and Windows.
- Check if Apple/Google have SSH clients on their AppStores which support hardware key based SSH keys and test.
- Find a solution for the macOS ssh-agent, if possible.